Strengthening Email Security Solutions & Validation Programs with a Disposable Emails Database

Email validation has become a necessity for organizations that aim to protect themselves against cybersecurity threats. The process becomes all the more relevant as 65% of attackers use phishing as a primary infection vector. That’s not a surprise, since attackers have long been weaponizing emails to serve as entry points for cyberattacks.
The ease with which threat actors can create disposable email addresses also contributes to the threat. In less than a minute, they can create a temporary email address with tons of providers, which they then use to send malware-laden and phishing messages to target victims. For this reason, a disposable email domain database can make email security vendors and email validation programs in general more robust and comprehensive. Let us elaborate on that.
2 Ways Email Solutions and Email Validation Program Can Benefit from the Integration of a Disposable Email Database
In a sense, temporary or disposable email services may serve as “privacy tools.” By using these services, people can avoid receiving spam emails on their real addresses. But fraudsters and other cybercriminals have also begun using temporary email addresses to execute attacks while keeping their identity hidden. Disposable email addresses have thus become akin to virtual private networks (VPNs) and proxy servers, which initially served a good cause.
Since threat actors have found a way to weaponize them, it’s usually best to filter disposable email addresses just as organizations block proxy users. By doing so, you weed out users who may have ill intentions or may not be interested in receiving follow-up brand communications. Sure, you may also sift out legitimate people who use disposable email addresses, but the danger of innocent employees falling for phishing emails far outweighs this.
1. Avoid Phishing by Blocking Disposable Email Addresses
In recent years, cybersecurity experts have seen a spike in attacks that use shared file services such as Office 365, OneDrive, and SharePoint. Employees would receive an email notification about their OneDrive account, for instance. Such emails could range from password expiry warnings to shared file notifications or voicemail alerts. Once the user clicks on the link embedded in the email, the attackers can get hold of his/her login credentials. In some instances, users may download malware in the guise of an innocent-looking file, thereby infecting their network.
Threat actors typically use an email domain that closely resembles that of the shared files service provider. And this is consistent with what we found in our disposable email domain database. For instance, when we searched for the word “drive” (as in OneDrive) on the database, which contained more than 25,000 disposable email domains, we found 52 matching records.
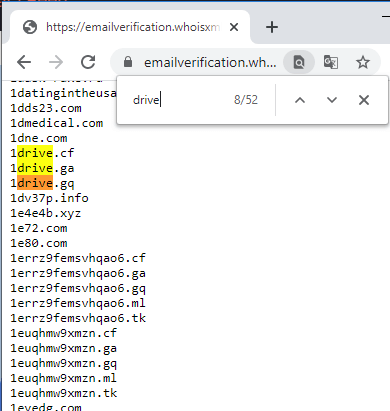
Of the 52 domains, nine could be masquerading as a shared files service domain:
- 0nedrive[.]cf
- 0nedrive[.]ga
- 0nedrive[.]gq
- 0nedrive[.]ml
- 0nedrive[.]tk
- 1drive[.]cf
- 1drive[.]ga
- 1drive[.]gq
- onedrive[.]web[.]id
- g00gledrive[.]ga
- skydrive[.]tk
- xyz-drive[.]info
An email validation program that doesn’t filter disposable email addresses may let all emails from these domains reach their intended recipients. That said, clients may end up receiving emails from 1drive[.]ga, a malicious domain, according to VirusTotal.
Of course, not all disposable email domains necessarily belong to bad actors, but not filtering them would also compromise clients and increase phishing risks.
2. Avoid Spam Emails
Google revealed that it now blocks 100 million spam emails daily on Gmail by using artificial intelligence. Put into perspective, however, this may not be much considering that 107 billion spam emails get sent every day.
A disposable email domain database can make email spam filters a lot more effective, as it immediately weeds out temporary email addresses mostly used by spammers.
Consider these spam messages with the subject line “Apple ID Locked.” The email domains used are lslp6dpp-08448929[.]id and vqeadkdp-56899194[.]jp, which are already suspicious on their own.
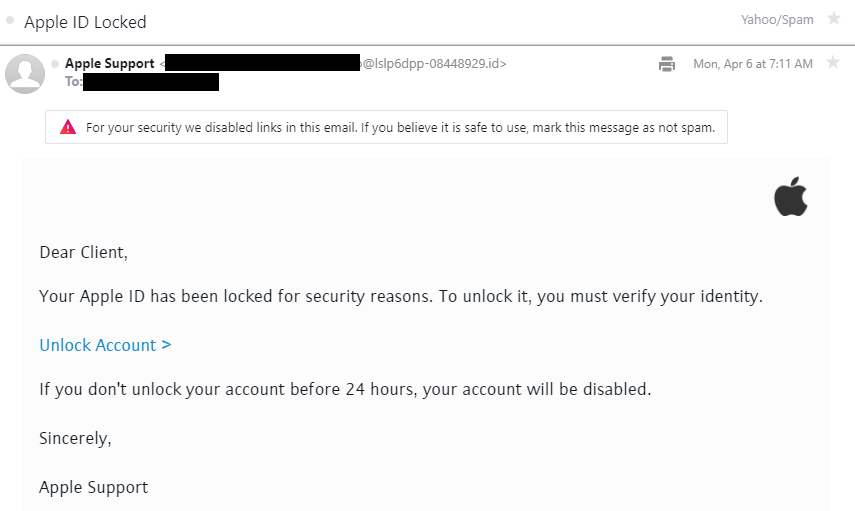
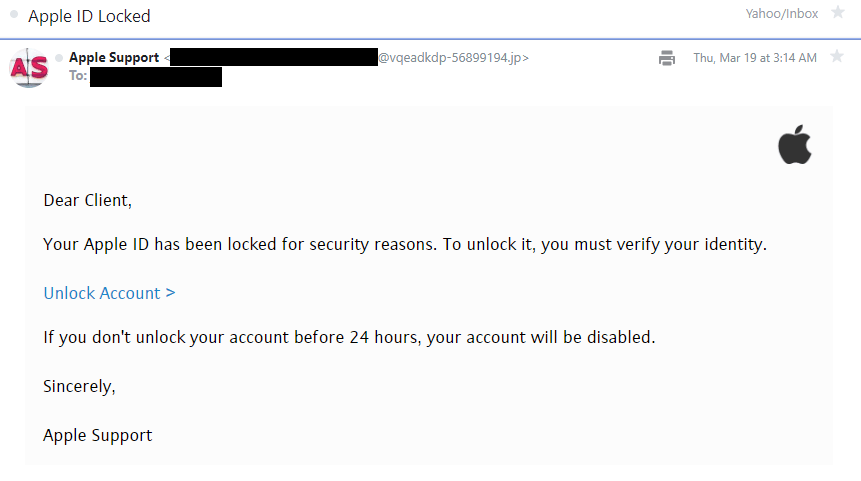
Both email domains are a combination of randomly generated alphanumeric characters, possibly generated by a disposable email service. Our disposable email domain database available for download contains hundreds of similar email domains. Below are some examples of them:
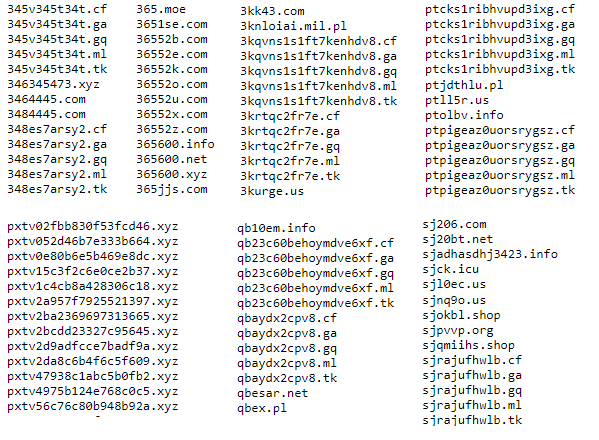
Integrating a disposable email domain database into an email validation tool would, therefore, help weed out similar spam emails.
How to Access the Disposable Email Domain Database
You can request access to the disposable email domain database here. If you don’t have an account yet, don’t hesitate to contact us. Once logged in, you will see a complete list of databases, arranged by date.
You can find the most recent database that contains all disposable email domains at the bottom of the index.
---
Disposable email addresses may have some legitimate uses, but since they can be used as attack vectors, security protocol usually ensures that these are blocked outright or are at least investigated before being granted access to an organization’s network. Therefore, an email validation application or program that aims to protect users from phishing and spam should also integrate a disposable email domain database.
Would you like to learn more about using a disposable email database and our other email validation products? Contact us for more information.





































